B.2 Asset Profile Worksheets
Use the worksheets in this section to document the analysis results during processes 4 through 8A for each critical asset. Collectively, these worksheets are called an asset profile; you should develop one asset profile for each critical asset.
The worksheets in this section generally appear in the order in which they are used. Any exceptions are specifically noted in the instructions for a section. The following asset profile worksheets are presented in this section:
Process 4
- Critical Asset Information - Security Requirements - Threat Profile Process 5
- System(s) of Interest - Key Classes of Components - Infrastructure Components to Examine Process 6
- Technological Vulnerability Summary - Actions and Recommendations Process 7
- Risk Impact Descriptions - Risk Evaluation Criteria Process 8
- Risk Mitigation Plans
B.2.1 Critical Asset Information
| Process 4 |
Activity: Select Critical Assets (Section 6.3) |
| Purpose |
To document information pertaining to the selection of a critical asset |
| Instructions |
Record the following information for the critical asset on the Critical Asset Information Worksheet:
The name of the asset and your rationale for selecting it A brief description of the critical asset, including who controls it, who is responsible for it, who uses it, and how it is used |
| Asset |
| Rationale for selection as a critical asset |
| Brief description |
B.2.2 Security Requirements
| Process 4 |
Activity: Refine Security Requirements for Critical Assets (Section 6.4) |
| Purpose |
To refine security requirements for the critical asset |
| Instructions |
Review any security requirements and areas of concern for the critical asset that were identified during processes 1 to 3. Also review any areas of concern. |
| |
Document the security requirements for the critical asset in the third column of the Security Requirements Worksheet. Use the following questions as prompts:
Confidentiality
- Is this asset proprietary or sensitive? - Does it contain personal information? - Should it be inaccessible to anyone who is not authorized to see it? - If the answer to any of these questions is yes, define the specific confidentiality requirement in the third column of the following table. Integrity
- Are authenticity, accuracy, and completeness important to this asset? If yes, define the specific integrity in the third column of the following table. Availability
- Is accessibility of the asset important? If yes, define the specific availability requirement in the third column of the following table. Other
- Are there any other security-related requirements that are important to this asset? If so, define them in the third column of the following table. |
| |
Determine the most important security requirement by examining trade-offs among the security requirements. Consider what would happen if confidentiality, integrity, or availability of the asset were violated. Document the most important security requirement in the "priority" column of the Security Requirements Worksheet. |
| Confidentiality |
|
|
| Integrity |
|
|
| Availability |
|
|
| Other |
|
|
B.2.3 Process 4: Threat Profile for Critical Asset
NOTE:
You do not complete the entire worksheet during one activity. First complete the threat profile for the critical asset (all fields in the Threat Profile Worksheet with the exception of the impact field). Record impact values on the Threat Profile Worksheet after evaluating impacts in Section B.2.11.
| Process 4 |
Activity: Identify Threats to Critical Assets (Section 6.5) |
| Purpose |
To identify the range of threats that affect the critical assets, creating a threat profile for the critical asset |
| Instructions |
Review the security requirements (Section B.2.2) and critical asset information (Section B.2.1). Also review any areas of concern for the critical asset identified during processes 1 to 3. |
| |
Answer the following question: Which branches correspond to an expressed area of concern? Mark these branches on the appropriate tree. |
| |
Review the remaining, unmarked branches (gaps) for threats that were not identified by the participants during processes 1 to 3. Consider the following questions:
For which of the remaining branches is there a more than negligible possibility of a threat to the asset? Mark these branches on the tree. For which of the remaining branches is there a negligible possibility or no possibility at all of a threat to the asset? Do not mark these branches. |
| |
Record notes to clarify threats as appropriate (i.e., branches that do not map to an existing area of concern). |
| |
A blank tree entitled "Other Problems (cont.)" is provided for you to record any unique threat actors not addressed in the threat profile. Complete the tree for any unique threats that apply to the critical asset. |
Threat Profile Worksheet: Human Actors Using Network Access
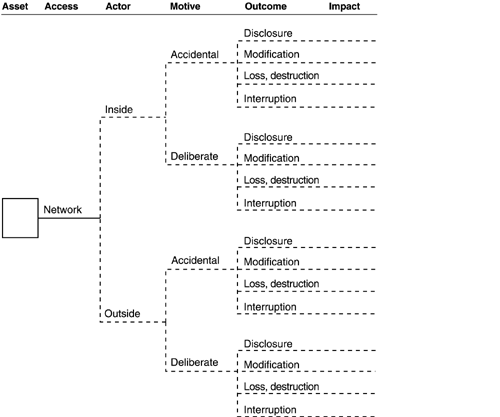
Threat Profile Worksheet: Human Actors Using Physical Access
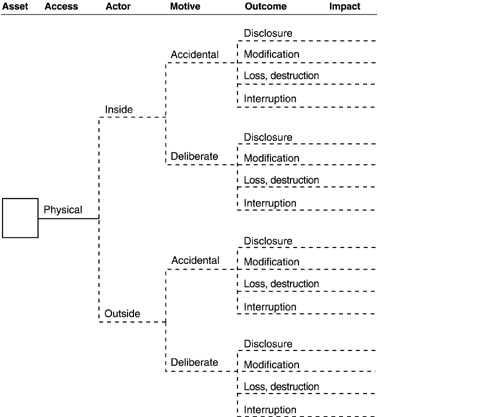
Threat Profile Worksheet: System Problems
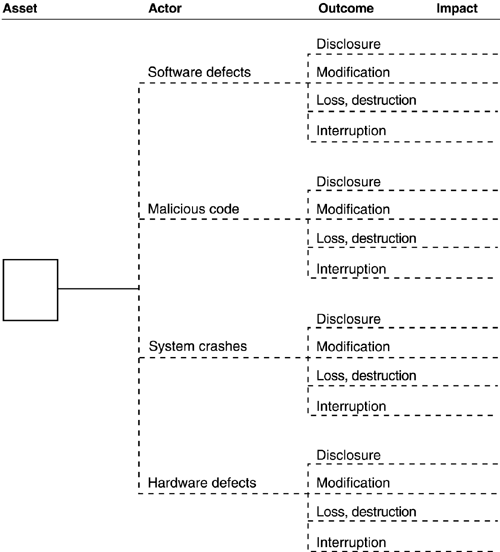
Threat Profile Worksheet: Other Problems

B.2.4 Process 5: System(s) of Interest
| Process 5 |
Activity: Identify Key Classes of Components (Section 7.2) |
| Purpose |
To identify the system most associated with the critical asset |
| Instructions |
Review the threat tree for human actors using network access in Section B.2.4. Use the following questions to guide your selection of the system(s) of interest.
Which system(s) is most closely linked to the critical asset? In which system(s) is the critical asset stored and processed? Where outside the system of interest do critical information assets move? Backup system? Off-site storage? Other? Based on the critical asset, which system(s) would be the target of a threat actor acting deliberately?
Record the system(s) of interest for the critical asset on the System(s) of Interest Worksheet.
|
| System(s) of Interest Worksheet |
| |
B.2.5 Process 5: Key Classes of Components
| Process 5 |
Activity: Identify Key Classes of Components (Section 7.2) |
| Purpose |
To identify key classes of components associated with the critical asset |
| Instructions |
Consider key classes of components that are part of or related to the system of interest. Use the following questions to guide your selection of the key classes of components.
Which types of components are part of the system of interest? Consider servers, networking components, security components, desktop workstations, home machines, laptops, storage devices, wireless components, and others. Which types of components are related to the system of interest? From which types of hosts can the system of interest be legitimately accessed? Desktop machines? Home machines? Laptops? Cellular phones? Handheld devices? Others? How could threat actors access the system of interest? Via the Internet? Via the internal network? Shared external networks? Wireless devices? Others? Which types of components could a threat actor use to access the system of interest? Which could serve as intermediate access points? Consider physical and network access to servers, networking components, security components, desktop workstations, home machines, laptops, storage devices, wireless components, and others. What other systems could a threat actor use to access the system of interest? Based on your answers to the above questions, which classes of components could be part of the threat scenarios?
Based on the answers to the questions, decide which key classes of components could be part of the threat scenarios. Mark an x in the box by each applicable class on the Key Components Worksheet.
|
| |
Record your rationale for selecting each key class on the Key Components Worksheet. |
B.2.6 Process 5: Infrastructure Components to Examine
| Process 5 |
Activity: Identify Infrastructure Components to Examine (Section 7.3) |
| Purpose |
To select specific components from each key class to evaluate for technology vulnerabilities |
| Instructions |
From the key classes of components documented on the Key Components Worksheet, select specific components from each key class to evaluate for technology vulnerabilities. Use the following questions to guide your selection of infrastructure components.
Is the infrastructure component typical of its class? How accessible is the infrastructure component? Is it "owned" by another organization? Is it a home machine? How critical is the infrastructure component to business operations? Will you be interrupting business operations when you evaluate the component? Will special permission or scheduling be required to evaluate the component?
Record the selected components, including their IP addresses and host/DNS names, on the Infrastructure Components to Examine Worksheet.
|
| |
Record the rationale for selecting each infrastructure component on the Infrastructure Components to Examine Worksheet. |
| |
Record the approach for evaluating each infrastructure component on the Infrastructure Components to Examine Worksheet. The approach should include the following information:
Who will perform the evaluation (e.g., IT staff, external experts) The selected tools (e.g., software, checklists, scripts) |
| System of interest |
|
|
|
| Systems/servers |
|
|
|
| Networking components |
|
|
|
| Security components |
|
|
|
| Desktop workstations |
|
|
|
| Home computers |
|
|
|
| Laptops |
|
|
|
| Storage devices |
|
|
|
| Wireless components |
|
|
|
| Others |
|
|
|
B.2.7 Process 6: Summarize Technology Vulnerabilities
| Process 6 |
Activity: Review Technology Vulnerabilities and Summarize Results (Section 8.3) |
| Purpose |
To document a summary of the technology vulnerability evaluation |
| Instructions |
For each evaluated component, review the proposed summary of the vulnerability evaluation. All analysis team members must understand
The types of vulnerabilities found and when they need to be addressed The potential effect on the critical assets How the technology vulnerabilities could be addressed (applying a patch, hardening a component, etc.)
Make any necessary changes to the preliminary summary, and record the results on the Technology Vulnerabilities Summary Worksheet. (You can record the information after the workshop.) The vulnerability summary contains the following information for each component that was evaluated:
The number of vulnerabilities to fix immediately (high-severity vulnerabilities) The number of vulnerabilities to fix soon (medium-severity vulnerabilities) The number of vulnerabilities to fix later (low-severity vulnerabilities) |
| |
Perform a gap analysis of the threat profile that you created during process 4. Turn to Section B.2.3, process 4: Threat Profile for Critical Asset. Reexamine the unmarked branches of the threat three for human actors using network access. Consider the following question: Do the technology vulnerabilities associated with the critical asset's key infrastructure components indicate that there is a more than negligible possibility of any additional threats to the asset?
Mark any additional branches on the appropriate trees in Section B.2.3. |
B.2.8 Process 6: Record Action Items
| Process 6 |
Activity: Review Technology Vulnerabilities and Summarize Results (Section 8.3) |
| Purpose |
To document any immediate or short-term actions or recommendations resulting from the technology vulnerability evaluation |
|
Instructions
|
Review the vulnerability summary that you documented in Section B.2.7. Record any immediate or short-term actions or recommendations on the Actions and Recommendations for Addressing Technology Vulnerabilities Worksheet.
Actions and recommendations are typically related to the technology vulnerabilities that were identified and the steps the organization needs to take to address those vulnerabilities.
|
B.2.9 Process 7: Risk Impact Descriptions
NOTE:
Do not complete the entire worksheet during one activity. First complete the create narrative description of the potential impacts on the organization (the "Impact Description" field in the Impacts on the Organization Worksheet). Record impact values on the Impacts on the Organization Worksheet after evaluating impacts in Section B.2.11.
| Process 7 |
Activity: Identify the Impact of Threats to Critical Assets (Section 9.2) |
| Purpose |
To create narrative descriptions of impacts on the organization based on threat outcomes |
| Instructions |
Potential impacts on your organization resulting from threats to your critical assets are generated according to threat outcome. Note that the second column in the Impacts on the Organization Worksheet contains questions to guide your creation of impact descriptions.
Record descriptions of the impacts on the organization for each outcome on the Impacts on the Organization Worksheet.
In general, the impact(s) on an organization for a given outcome will be the same regardless of the branch of the threat tree leading to that outcome. However, if there is a unique impact for a specific threat tree branch, note it in the description.
|
| Disclosure |
How could the organization's reputation be affected if this asset were disclosed? How could customer confidence be affected if this asset were disclosed? How could the health of customers be affected if this asset were disclosed? How could employee productivity be affected if this asset were disclosed? How could other users of this asset be affected if this asset were disclosed? What fines or legal penalties could be imposed as a result of disclosure of this asset? What lawsuits could be filed against the organization if this asset were disclosed? How could the organization be affected financially if this asset were disclosed? What other impacts could occur if this asset were disclosed (for example, ethical considerations, other legal/financial impacts)? |
|
|
| Modification |
How could the organization's reputation be affected if this asset were modified? How could customer confidence be affected if this asset were modified? How could the health of customers be affected if this asset were modified? How could employee productivity be affected if this asset were modified? How would other users of this asset be affected if this asset were modified? What fines or legal penalties could be imposed if this asset were modified? What lawsuits could be filed against the organization if this asset were modified? How could the organization be affected financially if this asset were modified? What other impacts could occur if this asset were modified (for example, ethical considerations, other legal/financial impacts)? |
|
|
| Destruction/Loss |
How could the organization's reputation be affected if this asset were destroyed, lost, or unavailable? How could customer confidence be affected if this asset were destroyed, lost, or unavailable? How could the health of customers be affected if this asset were destroyed, lost, or unavailable? How could employee productivity be affected if this asset were destroyed, lost, or unavailable? How would other users of this asset be affected if this asset were destroyed, lost, or unavailable? What fines or legal penalties could be imposed as a result of destruction, loss, or unavailability of this asset? What lawsuits could be filed against the organization if this asset were destroyed, lost, or unavailable? How could the organization be affected financially if this asset were destroyed, lost, or unavailable? What other impacts could occur if this asset were destroyed, lost, or unavailable (for example, ethical considerations, other legal/financial impacts)? |
|
|
| Interruption |
How could the organization's reputation be affected if access to this asset were unavailable? How could customer confidence be affected if access to this asset were unavailable? How could the health of customers be affected if access to this asset were unavailable? How could employee productivity be affected if access to this asset were unavailable? How would other users of this asset be affected if access to this asset were unavailable? What fines or legal penalties could be imposed as a result of unavailability of this asset? What lawsuits could be filed against the organization if access to this asset were unavailable? How could the organization be affected financially if access to this asset were unavailable? What other impacts could occur if access to this asset were unavailable (for example, ethical considerations, other legal/financial impacts)? |
|
|
B.2.10 Process 7: Risk Evaluation Criteria Worksheet
| Process 7 |
Activity: Create Risk Evaluation Criteria (Section 9.3) |
| Purpose |
To develop criteria to evaluate the impact descriptions that you created in Section B.2.9 |
| Instructions |
For each area of impact, define specific measures that define high, medium, and low risks for your organization. Use the following questions to guide your creation of impact values:
What defines a "high" impact on the organization? What defines a "medium" impact on the organization? What defines a "low" impact on the organization?
Record the criteria on the Evaluation Criteria Worksheet.
Note: You can use the evaluation criteria in Appendix A (Section 4) as an example. If you use the example as a guide, make sure that you modify it appropriately to make it meaningful and specific to you and your organization.
|
| Reputation/customer confidence |
|
|
|
| Life/health of customers |
|
|
|
| Productivity |
|
|
|
| Fines/legal penalties |
|
|
|
| Financial |
|
|
|
| Other |
|
|
|
B.2.11 Process 7: Risk Profile Worksheet
NOTE:
The tables and diagrams associated with the threat profiles and impact values already exist in this appendix. Only the instructions for completing them are listed here. See Section B.2.7 for threat profiles and Section B.2.9 for impact values.
| Process 7 |
Activity: Evaluate the Impact of Threats to Critical Assets (Section 9.4) |
| Purpose |
To evaluate the impact descriptions in Section B.2.9 against the evaluation criteria in Section B.2.10 |
| Instructions |
Evaluate the impact descriptions in Section B.2.9 against the evaluation criteria in Section B.2.10. Record the impact values for each impact description in the "Values" column on the Impacts on the Organization Worksheet (Section B.2.9). |
| |
Also record the impact values in the "Impact" column of the Threat Profile Worksheet (Section B.2.3). If more than one value is associated with any outcome, record all of them in the "Impact" column. For example, if disclosure has three statements describing the impact on the organization, one with a value of "high" and two with values of "medium," record "medium, high" in the "Impact" column. |
B.2.12 Process 8: Risk Mitigation Plans
| Process 8 |
Activity: Create Risk Mitigation Plans (Section 10.5) |
| Purpose |
To identify actions, or countermeasures, designed to counter the threats to the critical asset |
| Instructions |
Decide whether to accept or mitigate the risks to each critical asset. Typically, when you decide whether to accept or mitigate a risk, you base your decision on whether you want to take action to counteract the underlying threat. Make sure that you record your decisions on the Threat Profile Worksheet in Section B.2.3. Note that you must make a decision for each risk in the risk profile, which includes the following categories:
|
| |
For each risk that you decide to mitigate, create risk mitigation plans for the critical asset by selecting mitigation actions, or countermeasures, designed to counter the threats to the critical assets. Make sure that you review the survey results and contextual security practice information from processes 1 to 3 before creating mitigation plans. Use the following questions to guide your creation of risk mitigation plans:
What actions could you take to recognize or detect this threat type as it is occurring? What actions could you take to resist or prevent this threat type from occurring? What actions could you take to recover from this threat type if it occurs? What other actions could you take to address this threat type? How will you test or verify that this mitigation plan works and is effective? |
|
What actions could you take to recognize or detect this threat type as it is occurring?
What actions could you take to resist or prevent this threat type from occurring?
What actions could you take to recover from this threat type if it occurs?
What other actions could you take to address this threat type?
How will you test or verify that this mitigation plan works and is effective?
|
Consider administrative, physical, and technical actions that you could take. |
|
What actions could you take to recognize or detect this threat type as it is occurring?
What actions could you take to resist or prevent this threat type from occurring?
What actions could you take to recover from this threat type if it occurs?
What other actions could you take to address this threat type?
How will you test or verify that this mitigation plan works and is effective?
|
Consider administrative, physical, and technicalactions that you could take. |
|
What actions could you take to recognize or detect this threat type as it is occurring?
What actions could you take to resist or prevent this threat type from occurring?
What actions could you take to recover from this threat type if it occurs?
What other actions could you take to address this threat type?
How will you test or verify that this mitigation plan works and is effective?
|
Consider administrative, physical, and technicalactions that you could take. |
|
What actions could you take to recognize or detect this threat type as it is occurring?
What actions could you take to resist or prevent this threat type from occurring?
What actions could you take to recover from this threat type if it occurs?
What other actions could you take to address this threat type?
How will you test or verify that this mitigation plan works and is effective?
|
Consider administrative, physical, and technicalactions that you could take. |
|