3.9. Using the Encrypting File SystemWindows 2000 introduced the Encrypting File System (EFS), a way to scramble the contents of documents, other files, and even programs so that they become unreadable by anyone other than the person who encrypted them. Although EFS has merits in environments consisting of corporate desktop computers, the real boon is for laptops: because theft of laptops has been on the rise for almost a decade, there is a real risk in storing sensitive information on these mobile systems. If a laptop from a research and development representative were to fall into a competitor's hands, the cost of that loss would far exceed the retail price of a new laptop; indeed, the damage would be almost immeasurable. So, EFS is definitely an asset. How does EFS appear to the end user? It's nearly transparent in operation, though not as much in presentation. When you encrypt a document, Windows doesn't attempt to hide the document's presence on the disk. In fact, encrypted documents are outlined in blue with a normal default folder view. The real transparency comes when you open the document. The process goes as follows: from each individual file on a server's disk, Windows calculates a unique file encryption key. When a user selects to encrypt a file, the file encryption key is encrypted too, using the public key stored on the user's EFS certificate. (This public key is generated the first time a request to encrypt an object is submitted.) To decrypt a file, the file encryption key must first be decrypted, which happens when a specific user has a private key that corresponds with the public key. These private keys are not stored in the SAM; rather, they are held in a protected key store. Note that other users can be authorized to decrypt the file encryption key by using their own private key. If the keys match up correctlythat is, if the expected result is obtained from the mathematical processesthe filesystem object is decrypted transparently. If there is an error, and unexpected results are returned, the user is denied access and the object remains encrypted. The object is encrypted again when the user closes it. There are some limitations to note when using automatic encryption in the filesystem. For one, you can encrypt files and folders only on disks formatted with NTFS. Two, compressed files and folders cannot be encrypted; they will be uncompressed before the procedure. Three, you cannot encrypt files marked with the System attribute, as well as files in the system root folder. If you encrypt the parent folder when encrypting a single file or a single folder, all future additions to that folder will be encrypted automatically. But if you encrypt the folder only, objects in the folder at that point are not encrypted, though any future additions will be encrypted automatically. Additionally, when decrypting, if you select to decrypt a single file within an encrypted folder, future additions to that folder will not be encrypted.
3.9.1. Encrypting Files and FoldersTo encrypt a file or folder using the GUI, follow these steps:
To decrypt a file or folder, follow these steps:
3.9.2. Recovering Encrypted ObjectsIt can be somewhat disconcerting that, in emergency or recovery situations, encrypted files can be decrypted by a user other than the user who encrypted the file originally. This is actually a feature, and it really is quite secure. Designated user accounts, called recovery agent accounts , are issued recovery agent certificates with public keys and private keys upon their creation that are used for EFS data recovery operations. The Windows user accounts that function as recovery agent accounts are designated by a GPO or a local security policy object, depending on the machine's participation in a domain. By default, they are the highest-level administrator account available. Depending on the network environment of a particular machine, this is either the local administrator or the domain administrator. The private key from the appropriate agent certificate must be located on the computer where recovery operations are to be conducted. When a recovery agent certificate is issued, the certificate and private key are installed in the user profile for the user account that requested the certificate. An EFS file can contain more than one recovery agent account, and each EFS file can have a different private key. However, data recovery discloses only the encrypted data, not the user's private key or any other private keys for recovery. This ensures that no other private information is revealed to the recovery agent administrator unintentionally.
To view the recovery agents for an object, log in as the owner of the encrypted object. Then, right-click the object and select Properties. Click the Advanced button, which opens the Advanced Attributes dialog box. Click the Details button to bring up the Encryption Details box. The recovery agents for the specified object are listed in the bottom box. Figure 3-26 shows this. But what is in the top box of the Encryption Details dialog? This is a new feature of Windows Server 2003 which makes it quite a bit easier to enable other users to decrypt a file without them being recovery agents. By designating their user accounts in the top list, the users can access and use the file transparently. Simply click Add and select the users from the local computer or from a domain that should be able to access the file transparently. Figure 3-26. An object's recovery agents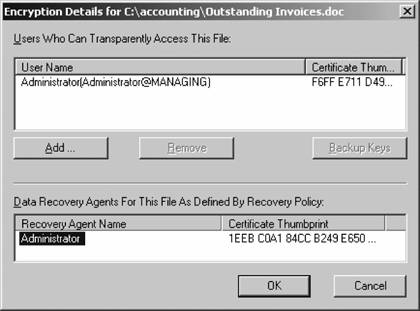
3.9.3. Protecting User Certificate IntegrityMicrosoft recommends that, to protect a user's certificate from thievery, users should export their personal certificate, save it to some sort of removable media, and then remove it entirely from the local computer. This is because although the encryption/decryption methods EFS uses are quite secure, if someone happens to make off with a machine and is able to log on with administrator credentials, he or she could modify the certificate configuration to allow him- or herself the ability to decrypt any files. Obviously, this is a problem. To perform this recommended procedure, take these steps:
The certificate will no longer reside on the computer from which you removed it. To reimport it to the same or a different computer, right-click inside the Certificates folder again, choose Import from the All Tasks menu, browse for your exported certificate file from the preceding list of steps, enter any necessary passwords protecting that certificate, choose a location for the key (usually the Personal folder is sufficient), and then click Finish. The key now resides on that computer. |