A.3 Risks and Mitigation Plans for Critical Assets
As a result of conducting the OCTAVE Method, we identified five assets that are critical to the survival and success of MedSite. We then defined the risks to these assets and developed mitigation plans to address these risks. The assets we identified as being the most critical, and our rationale for selecting them, are listed in Table A-3.
For each critical asset, we provide the following information in this report:
A.3.1 Paper Medical Records
Paper medical records are the official record of MedSite's patients' medical histories. While MedSite now stores and maintains much of its medical-related information on PIDS and other systems, providers still rely on paper medical records during all patient encounters. The security requirements for the paper medical records are defined in Table A-4. Integrity and availability are considered to be the most important security requirements for paper medical records.
Table A-5 summarizes the areas of concern for medical records organized by threat type.
Table A-4. Security Requirements for Paper Medical Records
|
Integrity:
Records must be kept accurate and complete and should be modified only by those with the appropriate authority.
|
|
Availability:
Access to records is required 24/7. They must be available for patient encounters.
|
| Confidentiality: Information should be kept confidential (restricted to those with "need to know"); Privacy Act. |
Table A-5. Areas of Concern for Paper Medical Records
| Human actors using physical access |
Medical records are left where they shouldn't be (in offices and labs). |
Disclosure |
| Data in medical records (e.g., physician SSN, credentials) could be used by someone to "forge" a prescription. |
Disclosure |
| Misfiling paperwork could allow unauthorized personnel to view another's records. |
Disclosure |
| Too many people are entering the wrong data, resulting in incorrect records, and/or there may be multiple files and records for an individual. |
Disclosure |
| Staff personnel could view medical records in an unauthorized or inappropriate manner. |
Disclosure |
| Information is deliberately released to outside personnel. |
Disclosure |
| Medical reports are signed out to patients, so anyone can potentially view, alter, or lose records. |
Disclosure
Loss/destruction
Modification
|
| Medical records could be signed out to the wrong person. |
Disclosure |
| Accidental problems with data entry can affect the integrity of information. |
Modification |
| Accidental mishandling by staff can lead to the destruction of physical medical records. |
Destruction/loss |
| Records are under "loose" control. There is no process to stop the patient from taking or modifying them and no mechanism to copy and release just what's needed. Integrity of record is compromised. |
Loss/destruction
Modification
|
| Patients could get poor-quality care or die if contradictory medications are prescribed or allergies are not accounted for. |
Modification
Loss/destruction
Interruption
|
| Loss of paper record can mean permanent loss of critical information. |
Loss/destruction |
| Other problems |
Configuration of facilities/layout allows inappropriate viewing of medical records. |
Disclosure |
| Roof leaks, water, fire, etc., could destroy the physical medical records. |
Loss/destruction |
| Hurricane evacuation procedures require movement of assets off the first floor of all facilities due to flooding concerns. |
Interruption |
We defined the specific impact on the organization of disclosure, modification, loss or destruction, and unavailability of paper medical records. We then evaluated these various impacts against a set of evaluation criteria (defined in Section 4) that define what constitutes a high, medium, and low impact for MedSite. The types of impact related to paper medical records are shown in Table A-6.
The risk profile for paper medical records is shown in Figures A-1 and A-2. There are two trees in the risk profile for paper medical records, each with a specific mitigation plan. Because network access and system problems do not affect the paper records, trees for these threat categories are not included in the risk profile.
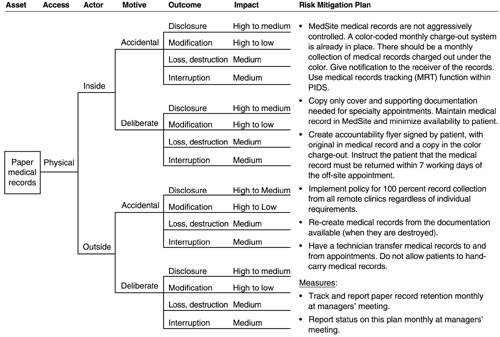
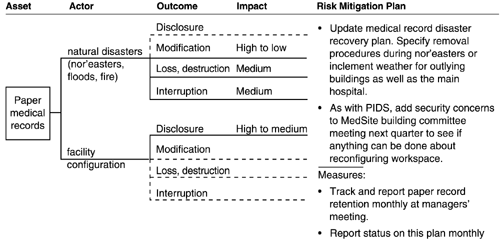
Table A-6. Types of Impact and Impact Values for Paper Medical Records
| Disclosure |
Loss of official accreditation. |
High |
| Health of patients could be affected by lack of continuity of care with PCM (primary care manager). |
High |
| Erratic visits to ER could result in incomplete diagnosis/prognosis and improper treatment. |
High |
| Patient with cancer and misfiled/nonfiled pathology report and no notification could file lawsuit against MedSite. |
High |
| Loss of credibility from our patients could ultimately result in patients seeking care from another source. |
Medium |
| Patient could maintain medical record at home due to lack of trust, and medical treatment could be incomplete in MedSite. |
Medium |
| Privacy violations can result in disclosure of medical treatment to unwanted sources, which could have negative results on patients, for example, divorce, loss of job, etc. |
Medium |
| Modification |
Deliberate modification could result in wrong diagnosis/treatment or death. |
High |
| Patients will seek care from another source. |
Medium |
| Loss of credibility with patients and the public. |
Low |
| Loss/destruction |
Loss of medical records would result in repeat of medical evaluations (lab, x-ray, etc.) for treatment, undue burden on patient, increased spending by MedSite, and decreased credibility. |
Medium |
| Interruption |
Lack of preplanning for known natural disasters would result in inability to provide services and a lack of faith in MedSite. |
Medium |
Human actors using physical access (Figure A-1) Other problems (Figure A-2)
A.3.2 Personal Computers
Personal computers are used to access PIDS and other systems. Our definition of personal computers includes all office, treatment room, and lab computers, as well as the laptops used by some physicians. The security requirements for personal computers are defined in the Table A-7. Availability is considered to be the most important security requirement.
Evaluation participants did not consider personal computers to be an important asset. Thus, no areas of concern were recorded for personal computers. (Note: After reviewing all information, the analysis team concluded that personal computers were a critical asset to MedSite.)
We defined specific types of impact on the organization resulting from disclosure, modification, loss or destruction, and unavailability of information on personal computers. We then evaluated these against a set of evaluation criteria (defined in Section 4) that define what constitutes a high, medium, and low impact for MedSite. The types of impact related to personal computers are shown in Table A-8.
Table A-7. Security Requirements for Personal Computers
|
Availability:
Computer assets should be available 24/7.
|
| Confidentiality: Patient information and Privacy Act information stored on PCs should be confidential. |
| Integrity: Software should be uniform and current. Information should be complete and accurate. |
| Other: All PCs should be password protected. Incident reporting procedures should be established. |
Table A-8. Types of Impact and Impact Values for Personal Computers
| Disclosure |
Personal computers left unattended offer a huge potential for violation of Privacy Act. Access, either deliberate or unintentional, is readily available. Patients who feel their privacy is not protected will seek care from other sources. It depends on what information is violated and to whom it is disclosed. |
Medium |
| Modification |
Modification of software could result in lost staff time, lost information, incorrect patient information, lost billing, etc. |
High |
| Loss/destruction |
Destruction or loss of the PCs results in failure to support our business. |
High |
| Interruption |
Any lengthy interruption of access to PCs results in our inability to perform our work. |
High |
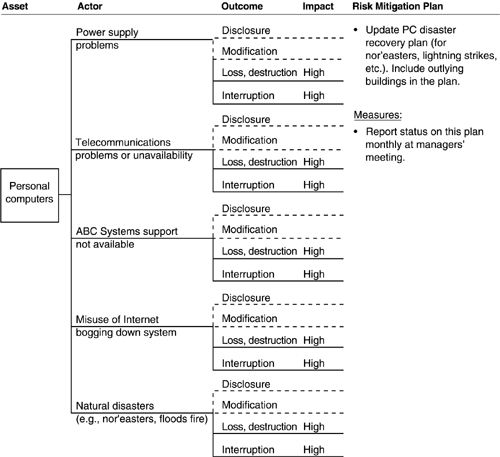
The risk profile for personal computers is shown in Figures A-3 through A-6. There are four trees in the risk profile, each with a specific mitigation plan.
Note: Staff members use massive mailing lists or misuse the Internet and bog down the systems. The network has crashed a few times from this behavior.
A.3.3 PIDS
PIDS is essential to the operation of MedSite. MedSite's operations are dependent on the information provided by this system. The security requirements for PIDS are defined in Table A-9. Availability is considered the most important security requirement.
Table A-9. Security Requirements for PIDS
|
Availability:
Access to information is required 24/7; it must be available for patient encounters. We need to have an adequate number of terminals for data entry operators.
|
| Confidentiality: Information should be kept confidential (restricted to those with "need to know"). Information is subject to the Privacy Act. |
| Integrity: Records must be kept accurate and complete. All information should be available for the patient encounter. Only authorized users should be allowed to modify information. |
Table A-10 summarizes the areas of concern for PIDS organized by threat type.
We defined specific types of impact on the organization resulting from disclosure, modification, loss or destruction, and unavailability of information on PIDS. We then evaluated these against a set of evaluation criteria (defined in Section 4) that define what constitutes a high, medium, and low impact for MedSite. The types of impact related to PIDS are shown in Table A-11.
Table A-10. Areas of Concern for PIDS
| Human actors using network |
Personnel access information that they are not authorized to use; access is used inappropriately, or legitimately accessed information is distributed inappropriately. |
Disclosure |
| Too many people have access to too much information. Role-based access builds over time and replacements inherit all of those access privileges. |
Disclosure |
| Access |
Too many people are entering the wrong data, resulting in incorrect records, and/or multiple files and records for an individual. |
Disclosure |
| Staff could intentionally enter erroneous data into PIDS. |
Disclosure Modification |
| The risk of an outside intrusion into PIDS is much higher than newer systems because of the need to bypass the firewall. |
Disclosure Modification |
| Accidental loss of any patient information is a concern. |
Loss/destruction |
| Patient could get poor-quality care or die if contradictory medications are prescribed or allergies are not accounted for. |
Modification Loss/destruction Interruption |
| Doctors and staff email sensitive patient information on an insecure LAN. |
Disclosure |
| PIDS can be attacked from outside. |
Disclosure Modification |
| Shared network drives contain sensitive patient and personnel information. |
Disclosure |
| Inherent flaws and vulnerabilities in critical applications could exploited. |
Modification Destruction/loss |
| Human actors using physical access |
Doctors leave PIDS screens on after they have left treatment rooms. Patients and others could gain access. Passwords, logout, time-out, and screen savers are inconsistently used. |
Disclosure |
| Doctors and staff often leave terminals/PCs unattended in exam rooms, introducing the possibility of unauthorized access. |
Disclosure |
| System problems |
PIDS is not compatible with newer systems, leading to system crashes. |
Interruption |
| Connectivity is an issue, including problems with availability of and access to PIDS. The uptime requirement in the contract is for the servers, not for our connectivity. |
Interruption |
| There are networking/connectivity issues. Access to PIDS is often restricted due to system crashes. |
Interruption |
| Instability of the local area network affects access to numerous systems and creates a backlog. |
Interruption |
| Other problems |
It's difficult to find and retain qualified personnel to help maintain PIDS. |
Interruption |
| Access to the majority of systems is supported by ABC Systems. They are responsible for hardware and software maintenance. We're concerned about our lack of control. |
Interruption |
| ABC Systems fails to recognize the importance of the Internet to the medical staff to access current best practice information. |
Interruption |
| Power outages, floods, and other external events can lead to a denial of access to PIDS. This essentially shuts the hospital down. |
Interruption |
| ABC Systems has many customers. They do not recognize the importance of the hospital. Priorities of the hospital are not understood. |
Interruption |
| The configuration of facilities/layout allows inappropriate viewing of systems and medical records by patients and visitors. |
Disclosure |
| Doctors and staff discuss patient issues and information in public areas. |
Disclosure |
| Hurricane evacuation procedures require removal of assets from the first floor of all facilities due to flooding concerns. |
Interruption |
The risk profile for PIDS is shown in Figures A-7 through A-10. There are four trees in the risk profile, each with a specific mitigation plan.
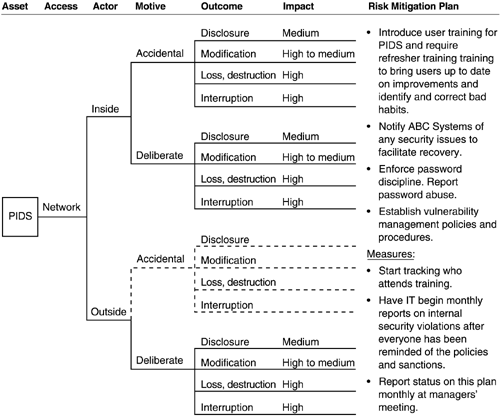
Table A-11. Types of Impact and Impact Values for PIDS
| Disclosure |
Failure to safeguard privacy would result in loss of credibility of medical treatment facility/organization. |
Medium |
| Modification |
Incorrect modifications could affect appointments and productivity. |
Medium |
| Work could be affected if modifications were made and we were unable to determine the extent easily. Verification of patient information would be tedious. |
Medium |
| Patient's life and health could be affected due to improper changes to treatment plans or medical records. |
High |
| Medical treatment facility could lose credibility. Loss of credibility could cause patients to seek care from another source. |
Medium |
| Loss/destruction |
The information in PIDS would be nearly impossible to reconstruct in a timely manner. Just trying to verify and reenter what was lost between the last backup and the present would take all our time and resources. |
High |
| Interruption |
An interruption could have a direct impact on our role in this community. We are rendered virtually helpless without PIDS capability. We have become computer-dependent in order to function. |
High |
| Our organization cannot deliver effective or efficient health care without PIDS. |
High |
A.3.4 ABC Systems
ABC Systems is responsible for the maintenance of PIDS and some of the other systems we have at MedSite. We rely on them to keep PIDS up and running. Because we depend on PIDS, we also depend on the services provided by ABC Systems. The security requirements at ABC Systems are defined in Table A-12. Availability is the most important security requirement. Note that confidentiality does not apply.
Evaluation participants did not identify specific areas of concern for ABC Systems. The analysis team constructed the threat profile during the process 4 workshop.
We defined the specific types of impact on the organization resulting from modification and unavailability of the service provided by ABC Systems. We then evaluated these against a set of evaluation criteria (defined in Section 4) that define what constitutes a high, medium, and low impact for MedSite. The types of impact related to PIDS are shown in Table A-13.
The risk profile for ABC Systems is shown in Figure A-11. There is only one tree in the risk profile:
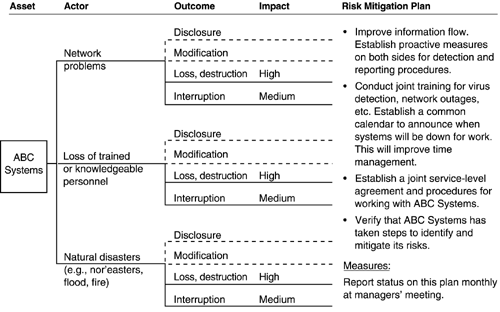
A.3.5 ECDS
The Emergency Care Data System (ECDS) is essential to the efficient operation of emergency rooms. It is also representative of systems we have that are linked to PIDS but are maintained by the local staff. ECDS is used to maintain and update patient records and billing for emergency cases, but it is not used during actual emergencies. The security requirements for ECDS are defined in Table A-14. Integrity and confidentiality are considered the most important security requirements.
Table A-12. Security Requirements for ABC Systems
|
Availability:
They must be available 24/7 to ensure that we are operational 24/7.
|
| Integrity: We require a consistent level of competence and training from ABC Systems personnel. |
| Confidentiality: N/A |
Table A-13. Types of Impact and Impact Values for ABC Systems
| Loss/destruction |
Destruction at ABC Systems' site would directly impact our effectiveness. |
High |
| Loss of knowledgeable personnel at ABC Systems would severely affect their quality of service to us. |
High |
| Interruption |
Lengthy interruption of support from ABC Systems could lead to the system being down or inaccessible for a long time, resulting in a direct impact on our day-to-day operations. |
Medium |
Table A-15 summarizes the areas of concern for PIDS organized by threat type.
We defined specific impacts on the organization resulting from disclosure, modification, loss or destruction, and unavailability of information on ECDS. We then evaluated these impacts against a set of evaluation criteria (defined in Section 4) that define what constitutes a high, medium, and low impact for MedSite. The types of impact related to PIDS are shown in Table A-16.
Table A-14. Security Requirements for ECDS
|
Integrity:
All information should be accurate and complete; this is essential for trend analysis and accounting.
|
|
Confidentiality:
Information should be kept confidential (restricted to those with "need to know"); Privacy Act.
|
| Availability: It must be available at the end of the day of the patient encounter. |
Table A-15. Areas of Concern for ECDS
| Human actors using network access |
Too many people are entering the wrong data, resulting in incorrect records, and/or there may be multiple files and records for an individual. |
Disclosure |
|
Internet connectivity is lost.
Systems are susceptible to malicious code and virus activity (in part due to the location/configuration of the firewall).
|
Interruption
Modification Loss/destruction Interruption
|
| Ultimate impact is on the quality of care. Patient could die if contradictory medications are prescribed or allergies are not accounted for. |
Modification Loss/destruction Interruption
|
| Other problems |
ABC Systems does not recognize the importance of the hospital/health care organization. Priorities of the hospital are not understood. |
Interruption |
The risk profile for ECDS is shown in Figures A-12 through A-15. There are four trees in the risk profile, each with a specific mitigation plan. We also checked for consistency between the risk profiles for PIDS and ECDS and identified several threats previously not identified for ECDS.
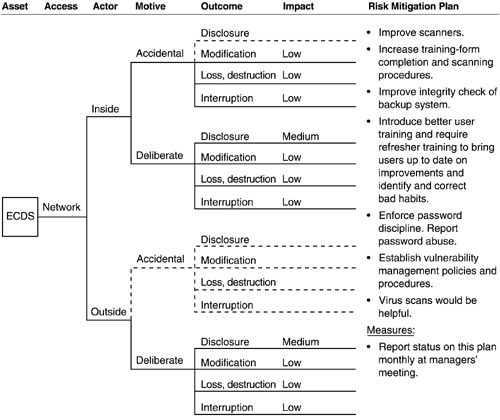
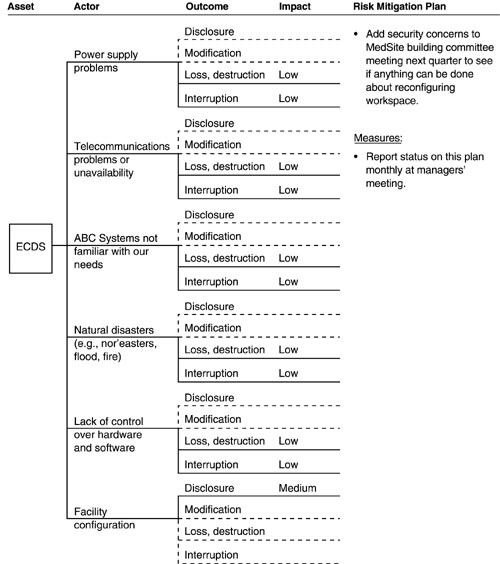
Table A-16. Types of Impact and Impact Values for ECDS
| Disclosure |
Privacy Act violation would occur if information were disclosed. |
Medium |
| Customer confidence would be affected by disclosure. |
Medium |
| Modification |
Heavy workload in facility leads to inadvertent modification and inaccurate data. Need to correct data affects manpower, resources, and budgeting. |
Low |
| Interruption |
Data entry delays following interruption of access would not be difficult to overcome, but doing so would take some clerical support time. |
Low |
| Loss/destruction |
Loss of information would result in duplication of effort to capture the data. |
Low |
|