A.4 Technology Vulnerability Evaluation Results and Recommended Actions
Once we identified the critical assets and the threats to those assets, we identified key infrastructure components to evaluate for technology vulnerabilities as part of phase 2 of the OCTAVE Method. This section summarizes our results and specific recommendations based on the results of phase 2. The summary provides a snapshot of how MedSite is managing its technology vulnerabilities.
Figure A-16 shows a high-level map of our computing infrastructure. As a part of the OCTAVE Method, we identified systems of interest for each critical asset and looked at access paths to identify key classes of components. From this, we selected specific instances of the key classes to evaluate for technology vulnerabilities.
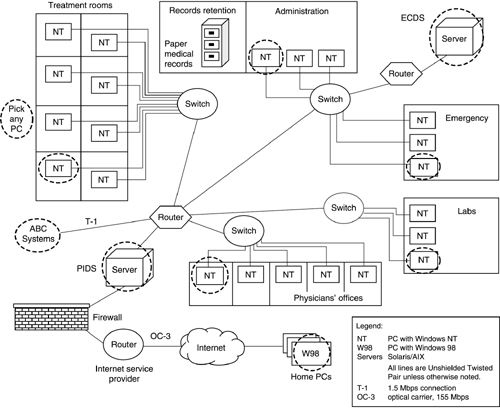
We examined network access paths for PIDS, ECDS, and personal computers. Figure A-17 shows the main access routes for accessing PIDS and highlights the key components we selected for the vulnerability evaluation. The network access paths for ECDS are similar; however, ECDS is not accessible from home PCs.
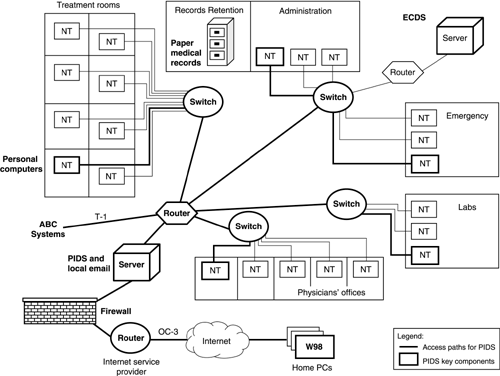
Although paper records do not have a network access path, printed email is sometimes included in paper records, as are printouts from systems such as PIDS. We wanted to evaluate the PDAs and the local email server, but at this point we could not determine how the PDAs used by the physicians were linking into the system. A representative from ABC Systems was not available to help, so this action should be dealt with as soon as possible.
Note that we did not conduct a physical vulnerability evaluation of MedSite; that was considered outside our scope of responsibility. However, we do recommend that a physical security audit or evaluation be conducted to verify that access to physical records is sufficient. Information that we gathered during the OCTAVE Method leads us to believe that paper medical records (stored in the Records Retention room) are physically vulnerable.
Key Components Per Asset
Table A-17 illustrates the system(s) of interest and key classes of components for each of the critical assets. There was some commonality among the key classes of components to be evaluated.
Table A-17. Systems of Interest and Key Classes of Components
| PIDS |
PIDS is its own system of interest. |
Servers Networking components Security components Desktop workstations Home computers |
| ECDS |
ECDS is its own system of interest. |
Servers Networking components Security components Desktop workstations |
| Personal Computers |
Personal computers are themselves the system of interest. (They are also a subsystem of the other systems such as PIDS and ECDS.) |
Servers Networking components Security components Desktop workstations Home computers |
Vulnerability Evaluation Approaches and Tools
Table A-18 shows specific components that were selected for the technology vulnerability evaluation, as well as the vulnerability evaluation approach for each component.
Evaluation Tools Results
Table A-19 summarizes the results of the technology vulnerability evaluation. Table A-20 provides the definitions for severity levels used in Table A-19.
Actions and Recommendations
During phase 2, we recorded recommendations and actions to consider based on the results of the technology vulnerability evaluation. Table A-21 shows those recommendations.
Table A-18. Infrastructure Components Examined
| Office PCs |
-----------------------
-----------------------
----------------------- |
ABC Systems personnel will be responsible for running all of the tools. MedSite's IT personnel will be present and will also get some on-the-job training |
Vulnerability scanner—Vulnerabilities-R-Found, version 6.73 |
These are common tools used at ABC Systems. Our IT personnel do not have the knowledge to run them but want to learn. |
| Home PCs |
----------------------- |
| Firewall |
----------------------- |
Network/Internet level tool—Improve-UR-Network, version 4.8 |
| PIDS server |
----------------------- |
| ECDS server |
----------------------- |
| Routers |
-----------------------
----------------------- |
Table A-19. Technology Vulnerability Evaluation Results
| PIDS client PCs—Windows 98 |
----------------------- |
Vulnerabilities-R-Found, v. 6.73 |
1 |
| |
----------------------- |
Vulnerabilities-R-Found, v. 6.73 |
3 medium
22 low
|
| |
----------------------- |
Vulnerabilities-R-Found, v. 6.73 |
3 medium
22 low
|
| Home PCs |
|
|
N—could not identify one whose owner was willing to allow the scan |
| Firewall |
----------------------- |
Improve-UR-Network, v.4.8 |
1 medium
5 low
|
| PIDS and mail server |
----------------------- |
Improve-UR-Network, v.4.8 |
3 high
21 medium
43 low
|
| ECDS server |
----------------------- |
Improve-UR-Network, v.4.8 |
9 medium
15 low
|
| Router 1 |
----------------------- |
Improve-UR-Network, v.4.8 |
3 low |
| Router 2 |
----------------------- |
Improve-UR-Network, v.4.8 |
3 low |
Table A-20. Severity Levels
| High-severity vulnerabilities |
Must be fixed immediately (within the next week) |
| Medium-severity vulnerabilities |
Must be fixed soon (within 1 month) |
| Low-severity vulnerabilities |
May be fixed later |
Table A-21. Phase 2 Recommendations
| Determine how and where PDAs are linking into the systems. Coordinate with ABC Systems and the physicians who have begun using PDAs. Handle after completion of OCTAVE. |
| Only a few of the vulnerabilities were of high severity. These will be fixed immediately by ABC Systems. However, all of the high-severity vulnerabilities were on the PIDS server, and that is some cause for concern, given the criticality of PIDS. |
| Most of the vulnerabilities were considered to be of medium severity. But the combination of many of them could result in either extensive interruption of access to PIDS or the loss/destruction of data on PIDS. This possibility should be considered when the risks and mitigation plans are being looked at in processes 7 and 8. The analysis team needs to consider the combined effects of the medium-severity vulnerabilities on the key components for PIDS, which is also the email server. Use as input to mitigation/protection strategy planning. |
| The same vulnerabilities show up on all of the PCs, which may mean a common configuration problem. It could also mean that the MedSite IT personnel and ABC Systems are not able to keep up with the latest revisions. Further investigation into the process IT uses to set up and maintain PCs is needed to determine whether the different configurations are a legacy or whether unapproved changes are being made. |
| The analysis team and ABC Systems also came to the conclusion that vulnerability management isn't being well executed, due to the high-severity vulnerabilities found on the PIDS server. ABC Systems personnel admitted they were not always able to run vulnerability scanners, but they were surprised at the number of high-and medium-severity vulnerabilities that were found. They thought the MedSite IT staff members were fixing these as soon as they were found. IT staff admitted that they did not know what to do with the vulnerability reports. Vulnerability management must be investigated and the weaknesses in procedure corrected. A plan will be needed to increase the knowledge and skills of IT and to improve the formality of ABC Systems' procedures. |
| Review policies for assessing home PCs. |
|